Searched by: Maurice Mosley
SearcherGeneral
Itend security login Clients Account Login
Links to all itend security login pages are given below in popularity order. Pages and websites related to itend security login are listed below too.
Published (Searched): 29th October, 2022
Last Updated: 30th October, 2022
Follow these easy steps to itend security login:
- Step 1. Go to itend security login page via official link below.
- Step 2. Login to website with your username and password
- Step 3. If you still can`t access itend security login then choose another link from the list below.
1. app.isecurityplus.com GB2. loginii.com
GB2. loginii.com AU3. www.securitymagazine.com
AU3. www.securitymagazine.com AU4. www.amazon.com
AU4. www.amazon.com US5. in-tendhost.co.uk
US5. in-tendhost.co.uk CA6. www.logintc.com
CA6. www.logintc.com AU7. www.fujitsu.com
AU7. www.fujitsu.com GB8. books.google.ru
GB8. books.google.ru US9. books.google.ru
US9. books.google.ru AU10. books.google.ru
AU10. books.google.ru CA
CA
Added by: Milton Patel
Explainer
iSecurity+: Log In
Login or create an account to accept your friend's invitation. Log In. Enter username. Enter password. Login incorrect. Please try again.
Url: https://app.isecurityplus.com/
 GB
GBPopular in
Up
Service Status
0h ago
Last Checked
Added by: Fernanda Mccarthy
Explainer
Itend Security Login - Loginii.com
Find top login links for Itend Security Login page directly. Alongside, helpful links regarding Itend Security Login are also present.
Url: https://loginii.com/itend-security
 AU
AUPopular in
Up
Service Status
0h ago
Last Checked
Added by: Paityn Ewing
Explainer
Fake login pages are spoofing the world's largest brands ...
Fake login pages are spoofing the world's largest brands – Where does it end? November 12, 2020. Ian Baxter. KEYWORDS cyber security / enterprise cyber ...
Url: https://www.securitymagazine.com/articles/93465-fake-login-pages-are-spoofing-the-worlds-largest-brands-
 AU
AUPopular in
Up
Service Status
0h ago
Last Checked
Added by: Lincoln Harding
Explainer
Tend Secure Cameras and Events: Alexa Skills - Amazon.com
Tend Secure Cameras and Events. Get this Skill. Sign In. By enabling, this skill can be accessed on all your ... “Alexa, ask Tend Secure to turn on recording.”.
Url: https://www.amazon.com/Tend-Secure-Cameras-and-Events/dp/B077P2KQZZ
 US
USPopular in
Up
Service Status
0h ago
Last Checked
Added by: Zachery Olsen
Explainer
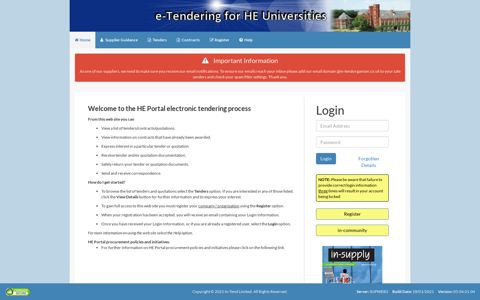
In-Tend Electronic Tendering Site - Home
Login. Forgotten Details. NOTE: Please be aware that failure to provide correct login information three times will result in your account being locked. Register.
Url: https://in-tendhost.co.uk/he/
 CA
CAPopular in
Up
Service Status
0h ago
Last Checked
Added by: Laci Bryant
Explainer
Free Trial | LoginTC - Simple and Secure Two-Factor ...
Step 2: Connect Your Existing Infrastructure. LoginTC integrates your IT end-points: VPNs, Citrix, Web Access Managers, CMS, and Web applications without ...
Url: https://www.logintc.com/get-started/
 AU
AUPopular in
Up
Service Status
0h ago
Last Checked
Added by: Leonardo Davis
Explainer
Fujitsu PalmSecure ID Login : Fujitsu EMEIA
But there is a simpler and, above all, more secure way! PalmSecure™ ID Login offers you the possibility to log in securely and at the same time very uncomplicated ...
Url: https://www.fujitsu.com/emeia/services/security/offerings/biometrics/palmsecure/id-login/
 GB
GBPopular in
Up
Service Status
0h ago
Last Checked
Added by: Karson Kline
Explainer
CCNA Security 640-554 Official Cert Guide: CCNA Sec 640-554 ...
the building from the outside through that door, the security guard is going to go from top to bottom through the list until either there is ... This is an example of an access list being applied inbound on a specific interface. ... That is it, end of story.
Url: https://books.google.ru/books?id=OhOZZCmSNwEC&pg=PA242&lpg=PA242&dq=itend security login&source=bl&ots=m
 US
USPopular in
Up
Service Status
0h ago
Last Checked
Added by: Stacy Santiago
Explainer
Information Security Management Handbook on CD-ROM, 2006 Edition
Although external threat is growing, the internal threat to data security remains ... can be accessed is by satisfying the access control policy of the VPN server. ... the concept of building in security from the beginning, and using it end-to-end.
Url: https://books.google.ru/books?id=5sIJ4Ho5yLUC&pg=PT1015&lpg=PT1015&dq=itend security login&source=bl&ots
 AU
AUPopular in
Up
Service Status
0h ago
Last Checked
Added by: Cadence Fisher
Explainer
Information Security Management Handbook, Fifth Edition
Although external threat is growing, the internal threat to data security remains ... can be accessed is by satisfying the access control policy of the VPN server. ... the concept of building in security from the beginning, and using it end-to-end.
Url: https://books.google.ru/books?id=D_h4AgAAQBAJ&pg=PA640&lpg=PA640&dq=itend security login&source=bl&ots=-
 CA
CAPopular in
Up
Service Status
0h ago
Last Checked
Troubleshoot:
- Make sure the CAPS Lock is off.
- Clear history for that site.
- Clear all cookies and the cache.
- Make sure the internet connection is available.
- In case you have forgot your password - reset it.
- If you still can’t get into your account, contact website support.
11
30th October, 2022
369
11
Active
8
Answers
7
Images
37
Users